HyTrust Data Control
With recent surveys showing that over 50% of IT managers withhold sensitive data from the cloud, it is clear that there is a need and desire for a solution that allows you to deploy even sensitive data to the cloud. Indeed, a look at many recent breaches reveals that on many cases user account and password data was stored in plaintext with no encryption. Fortunately addressing such shortcomings can be relatively easy with it taking only seconds to install the HyTrust encryption agent and powerful key management capabilities contributing to the overall operational transparency of the solution.
HyTrust Cloud control
Organizations are moving to hybrid multi-cloud architectures, but struggle with achieving consistent security and compliance while not slowing down application innovation.
CloudControl reduces risk by providing unified security and compliance controls across hybrid multi-clouds, lowering operational overhead and facilitating workload agility.
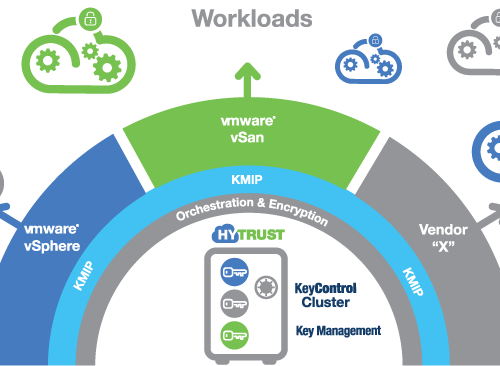
HyTrust Key Control
Universal Key Management System for Encrypted Workloads.
Encrypting workloads helps enterprises to ensure their data is protected, even if the data falls into the wrong hands. One of the challenges of workload encryption is to scale the management of tens of thousands of encryption keys, for workloads that may even be hosted on different platforms.
HyTrust KeyControl enables enterprises to easily manage all their encryption keys at scale, how often they rotate them, and how they are shared securely.
HyTrust Cloud advisor
Lets face it: We live in a data-driven world. Your data is your most valuable corporate asset. Yet, four out of five organizations don’t know where their sensitive data is located or how to secure it.
It should be no surprise that without a comprehensive understanding of your data it’s impossible to completely secure it against cyberhacking, insider threats, general misuse, obscurity, or a wide variety of other risks.
By taking a proactive approach to understanding your data and data management policies, you stand a far better chance of preventing the next data breach and passing your next audit.

